Monday, March 26, 2012
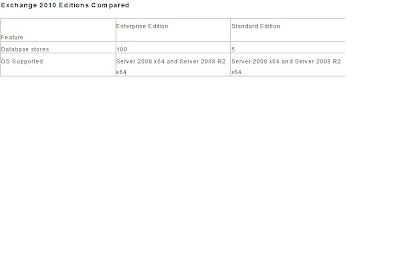
Exchange edition compared

Tuesday, August 9, 2011
Escape from Expensive Licensing: RemoteApp
Nowadays, the cost involved in the user license for some applications are too high. But off course we cannot avoid this, but for an extent can be minimized smartly by using the RemoteApp. Though RemoteApp is not the first to exist, prior can be done via Citrix.
For example just think about common application used internally which has the per user license, can be published in RemoteApp, in turn used for n number of users.
But there are high end application cover this loop holes, their licensing terms have the virtualizing license terms and also blocked the feasibility of terminal session publish options. As long as the application allows as to work smoothly in RemoteApp, no harm in using it. This can save some serious money for your organization.
Thanks
Logan
Directory Partitions in Active Directory:
BCP vs DR
Saturday, June 25, 2011
JBOD vs RAID : Storage
Thursday, June 16, 2011
Kaspersky 8 Update Availability – forefront SP2 Rollup
Wednesday, June 15, 2011
BB device troubleshooting - client side
Blackberry OS Installation/Upgradation:
Monday, March 7, 2011
New features in the unified messaging of Exchange 2010
Hi Friends,
In this article, let’s see the new features in the unified messaging of Exchange 2010.
The following is a list of new Unified Messaging features that have been included in Exchange 2010:
- Personal auto attendants (call answering rules)
- Additional language support including in Outlook Voice Access and Voice Mail Preview
- Enhancements to name lookup from caller ID
- Voice Mail Preview
- Messaging Waiting Indicator
- Missed call and voice mail notifications using text messaging (SMS)
- Protected Voice Mail
- Built-in Unified Messaging administrative roles
For more information about the new Unified Messaging functionality and new voice mail features.
Functional Descriptions
Voice Mail Preview: Exchange Server 2010 will facilitate the cumbersome task of navigating through voice messages. With Exchange Server 2010 speech-to-text translation, the user can read the contents of the audio recording in the same fashion they would read an e-mail. Furthermore, if the resulting voice messages are opened using Microsoft Office Outlook 2010, the text of the voice mail preview will become "actionable". Recognized names, contacts, and phone numbers will all be identified with icons that the user can select to add contacts, call using Office Communicator, or send e-mail. To facilitate navigation of the audio, clicking in the text will cause the voice mail to jump to that word and continue playing.
Protected Voice Mail: Exchange Server 2010 solves the problem of unauthorized distribution of the messages by securing the message content, specifying the users who may access that content, and the operations that they may perform on it. It uses Active Directory Rights Management Services to apply Do Not Forward permissions to voice messages that are designated either by the sender (by marking the message as private) or by administrative policy. This prevents the forwarding of protected voice mails in a playable form to unauthorized persons, whatever the mail client used.
Message Waiting Indicator (MWI): Now with Unified Messaging, users are notified of the presence of new/unread voice mail by lighting the lamp and providing a count on their supported desk phone. Additionally, users can configure their text messaging notification account to receive the beginning content of the voice mail preview in the SMS.
Auto Attendant: Users are often looking for a person in an organization, but are unsure of the extension or exact phone information. Exchange Unified Messaging's Auto Attendant enables users to easily navigate to the person they are trying to reach when calling an organization with either the telephone keypad or speech inputs to navigate the menu structure, place a call to a user, or locate a user and then place a call to that user. An auto attendant gives you the ability to:
- Create a customizable set of menus for callers
- Define informational greetings, business hours greetings, non-business hours greetings, and holiday schedules
- Describe how to search the organization's directory and connect to a user's extension
- Enable external users to call the operator
Call Answering Rules: Unified Messaging enables users to have more control over their call flows. For a salesman, this could mean the difference between sending an important sales lead to his voice mail instead of finding him on his cell phone or home phone. Call Answering Rules present callers with custom greetings, Find-Me, and call transfer options, in addition to leaving a voice mail. Moreover, these rules can be preceded by conditions (such as caller-IDs, time-of -day and Exchange free/busy status), giving end-users greater control over how they can be reached over the phone.
Outlook Voice Access: Users now have control over their Inbox with Outlook Voice Access via a telephone keypad or voice inputs. This enables anywhere access to their mailbox when a user is away from a computer or Internet-connected device. Now users no longer have need to worry about being late for appointments or being disconnected when traveling, as they can instantly call into their mailbox to manage their calendar, contacts, and e-mail.
Enhanced Caller ID: Users can get more context and information about their callers with Enhanced Caller ID. Callers are often not a part of a user contact list or organization's directory. For these cases, Windows Live Search will be used to try and determine the calling party. If a match is found, the result will be placed on the calling line of the message to better inform the user where the call came from.
Language Support: More users can now listen to and interact with their e-mail and voice mail in their native language or dialect. Exchange Server 2010 offers a broad range of language support with support for 16 languages including three varieties of English, plus Mandarin, Cantonese, European and North American versions of Spanish and French, and several other European languages.
Thanks
Logan


